I have been pointed to a comment here. According to /u/singhnsk this is a kill switch for devices locked to a specific carrier, not a telemetry. So, the issue is kill switch preinstalled on (some?) devices in (probably?) all regions.
With permission, I am quoting the author in full here:
I have already checked it in the month of January. It is a PhoneProtect app that is designed to lock a financed phone in case the debt is not paid timely. Here is what I/We found in the app's code. I am rooted. So, I can do any additional tests which the OP may require (if he desires, he's welcome to contact).
It needs SMS access so that the carrier can block/unblock the phone even if the user has disabled data connection by just sending a smart SMS code that the app can pick up.
co.sitic.pp
[2:14 PM, 2/1/2020] Para desbloquearlo debes pagar la deuda vencida por el
financiamiento del equipo. Si ya pagaste comun\u00edcate con Servicio
al Cliente e ingresa el c\u00f3digo de desbloqueo.Translation: To unlock it you must pay the debt due for the financing of the equipment. If you have already paid, contact Customer Service and enter the unlock code.
So, not everything can be Telemetry. It seems the app pings the server to get the latest update if it should block the phone or not. The app's source suggests that in such a case the app will require the user to enter an unlock code else the access to the device will be restricted.
Edit: Claro (as OP said the app pings to claro.com.co domain): Claro Americas is a Brazilian company part of América Móvil, a Mexican telecom group serving clients in Argentina, Brazil, Chile, Colombia, Costa Rica, the Dominican Republic, Ecuador, El Salvador, Guatemala, Honduras, Nicaragua, Panama, Paraguay, Peru, Puerto Rico and Uruguay. The poster didn't specify his region. If he is in one of those regions and then the app pings that domain, then it is even less of an issue.
Edit 2: Translation of more Spanish text from the app:
"Dear user, we inform you that your payment deadline expires. We invite you
to make your payment by entering mitelcel.com or by telephone by
calling * 111, opt. 1, opt. 2. In case of not making your payment in
the following. 24 hrs., Your service will be suspended and your
terminal equipment disabled. The service and equipment will be
restored once you have made your payment. Information in * 111. "
"Your equipment has been disabled due to your debit. To rehabilitate your
equipment and continue using it, we invite you to make your payment
as soon as possible. You can make the payment online at www.mitelcel
.com, through the App My Telcel or in Customer Service Centers.For
information, dial * 123 or * 121 in Mexico City, Mexico City, Hidalgo
and Morelos or * 111 from the rest of the In order to avoid delays
and your equipment being disabled, we invite you to direct your
payment to an odd credit card. More information at
www.telcel.com/paymentspayment."So, an app that can block financed phones (if the due not paid timely), is connecting to the carrier's domain to get some data, is not "malware". Agree though that it is a wrong inclusion for regions not covered by that carrier.
A bit later, an official reply has been posted confirming this and stating that this app will be removed soon with an update to Android 10.
On 12/03/2020, there is no reply yet about HMD Global telemetry in devices. This article will be updated.
Everything posted here is author's personal opinion.
I have recently purchased Nokia 6.2 and wanted to check if it sends any data somewhere, considering what happened with previous models
First, I noticed approx. daily connection to dapi.hmdglobal.net
This is a Google Cloud that could belong to a company behind Nokia - HMD Global.
But the Privacy policy in my phone only speaks of "activation" process, not of daily diagnostics data.
So I used developer tools to remove the following packages (warning: this may break your device, I am not responsible for any consequences)
com.hmdglobal.enterprise.api
com.qualcomm.qti.qms.service.telemetry
com.qualcomm.qti.qmmi
com.qualcomm.qti.qdma
Before removing them, I used APK Extractor to save APK files just in case it breaks my phone and I may be able to attempt reinstall. This part comes into play later.
The first was my blind guess about what exactly connects to dapi.hmdglobal.net
The next 3 I found mentioned in various forums for other devices as "safe to remove", however, I have not seen any telemetry sent to Qualcomm or anywhere else, except what I mention next.
After removing these packages, I noticed that there are some remaining unknown connections my device attempts several times per day.
They are all done in same order, one right after the other:
www.pppefa.com
www.ppmxfa.com
www.forcis.claro.com.co
After some investigation, I found that the first two domains point to some Microsoft Cloud servers rented in US.
The last one most probably belongs to Colombian telecom company, and this is where it becomes interesting.
After many hours of fruitless removing of different apps in my attempt so stop it, I suddenly remembered something.
When I used APK Extractor previously, there was an empty first line with some generic icon where an app icon should have been.
I went there again and indeed, this is a hidden system app, that you can not see in the list of all apps in Settings, normally. But it turns out, you can see it in Data usage (after it successfully sends some data using your mobile connection).
The name of the app is deliberately left empty to hide it, but if you click it in Data usage, you can see that this app is co.sitic.pp
, which can receive SMS, can make calls, and has access to internet.
As with all Android apps, you can reverse read the name to guess what it is.
Turns out, sitic.com.co is a Colombian company, who "are leaders in innovation and create mobile and WEB applications for new products and services." (credit goes to Google Translate)
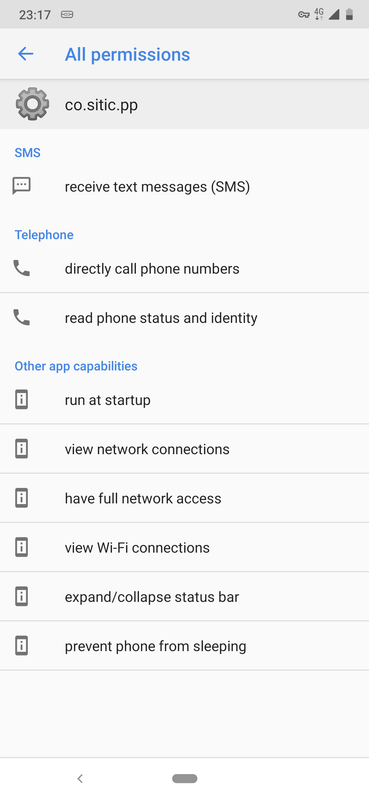
In other words, this app is a 3rd party telemetry, hidden from user, not mentioned in the Privacy policy, that has access to SMS.
This looks very bad and I really hope this is a malware injected by factory and not something knowingly distributed by Nokia, HMD Global, the EU company.
After removing the co.sitic.pp
app, requests to Microsoft Cloud and Colombia stopped.
I was later pointed to a German forum, where (I believe) it was first found in a Nokia 7.2 device.
So, we have it confirmed in 2 devices in 2 different countries.
Updated 12/03/2020: in total, from forum posts and personal messages, I now have confirmations of co.sitic.pp
app present from users in Germany, Estonia, Russia and India.
On German forum they contacted Nokia (I assume support) but got tired exchanging emails for weeks without any result.
On 02/03/2020 I have requested an official reply from Nokia and HMD Global via press.services@nokia.com and press@hmdglobal.com and waiting for reply.
Since I am not a journalist, I may never get one. This is also posted on Nokia community forum.
TLDR: 3rd party telemetry is found in Nokia 6.2 and 7.2 devices, is hidden from user, has access to SMS, and sends data to Microsoft Cloud in US and a server in Colombia.
It is probably supplied by SITIC S.A.S., a Colombian company, and looks more like a malware than a telemetry.
Nokia, Google, Microsoft trademarks are the property of their respective owners
| Github profile |